Virus Clean for Windows- Virus Clean for Mac
Virus Clean for Windows- Virus Clean for Mac
When need this service:
How to Tell if Your Computer Is Infected
It’s been 40 years since the first computer virus was unleashed, and widespread adoption of online connectivity has made their distribution a daily occurrence. Numerous malware and spyware incarnations can attack your systems, including newly launched zero-day attacks, botnets, viruses, worms, Trojan horses, adware and ransomware. Each can cause significant system damage to your system.
A virus or malware will negatively impact your system, leaving you vulnerable to fraud, but the degree of impact depends on the infection’s type and scope. Here are some of the possible consequences of a computer infection:
- Loss of performance: Malware can make your computer process things more slowly, hogging system resources and taking far longer than usual to get work done.
- Loss of bandwidth: Botnets are networks of computers serving a central remote system, often distributing large volumes of data and consuming all broadband bandwidth.
- Loss of function: In extreme cases, the virus can degrade your computer performance or programming so severely that you can no longer use your machine.
- Exposure to other dangerous software: The purpose of some malware is to entice you to download even more dangerous software.
- Loss of information: Viruses might delete stored files or data, while ransomware may destroy your entire hard drive if specific demands aren’t met.
- Breach of privacy: Viruses sometimes seek to gather information for identity theft or fraud. This could result in financial losses if your accounts are breached and even punitive fines if your firm didn’t follow local and state business regulations surrounding data privacy.
- Computer viruses are designed to attack your system. They spread from machine to machine via shared links, uploaded and downloaded files, or compromised websites. People spread viruses when they link and share carelessly or don’t use proper antivirus protection.
- Worms are similar to viruses, but they don’t need human help to spread. They’re programmed to move across computer networks on their own.
- Adware, spyware and ransomware are designed to track what you do online, gather data about you, and even steal your data and hold it hostage.
Here are 10 signs your computer is infected:
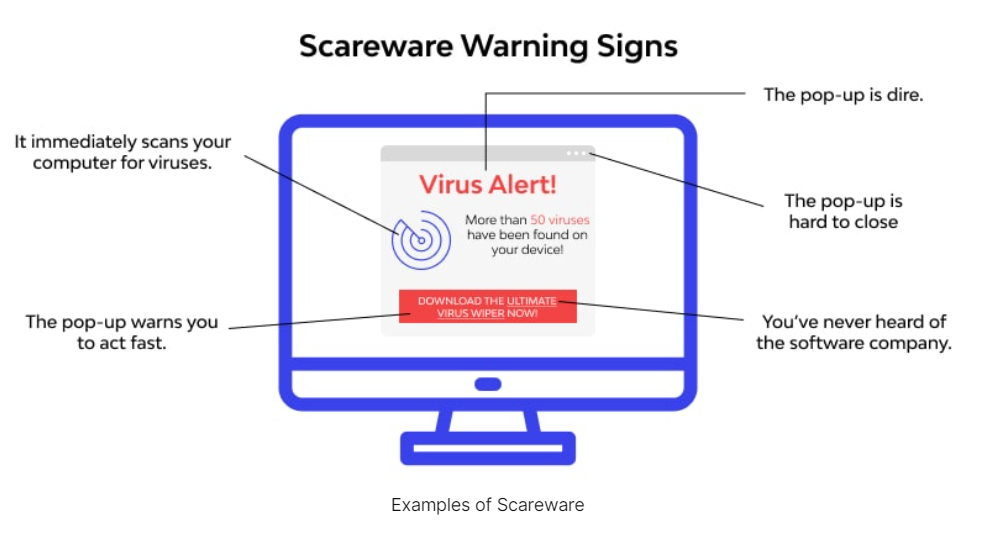
1. Unexpected pop-up windows
Unexpected or unusual dialog boxes and windows can be a bad sign. Fake virus warnings claim you have security threats on your computer and usually prompt you to click a link or call a number.
Legitimate protection software, such as Windows Defender and virus-scanning programs, will never prompt you to call a customer service number.
2. Random sounds
Infected computers are often programmed to respond with an audio signal to things you can’t control.
If you regularly hear chimes and bells from your computer that seem phantom, your computer may have a virus or malware infection.
3. Unexplained file or folder changes
Your files might be missing, or the icons and content of your files may be different. Your computer won’t make these types of changes to your files unless you have a virus or technical problem, though corrupted browser bookmarks shouldn’t be regarded as a warning sign. It’s common for bookmark icons to become jumbled by a browser such as Chrome.
4. Slow operation
Pay attention to whether your computer is running more slowly than usual, especially if its hard drive light (if it has one) is constantly on or its fan is operating at full speed. This suggests the computer’s resources are being redirected away from legitimate programs.
Money is a massive incentive for cybercriminals.
5. Random connections to unknown websites
Another sign of an infection is when your legitimate antivirus software alerts you that an application is trying to connect to a website you’ve never heard of.
In general, your computer doesn’t make its own connections; someone has to initiate them. If you didn’t initiate these connections, problematic software could be doing it for you.
6. Unexpected images
You might see pornographic images pop up or replace benign images, such as photos on news sites. A related sign that your computer is infected is the constant appearance of pop-up ads for sites you don’t usually visit.
7. Inability to download antivirus programs or updates
Computer viruses aren’t living things, but some are programmed with a self-preservation instinct. For the average computer user, the best way to kill a virus is via an antivirus scan. If you’re having trouble downloading and installing the antivirus software, or you’re unable to update your existing program, the virus may be defending itself. Some antivirus software solutions provide rescue disks to scan and clean an infected PC.
8. Spam sent from your email address or social media
Malware can work in many different ways. One variant sends random messages to your contacts list. This infection spreads across the internet by tricking people into clicking on an infected link. The link then spreads the malware to that person, who unwittingly spreads it throughout their friend list. By logging out of your accounts, creating strong passwords, and implementing security measures like two-factor authentication, you can thwart any further intrusion.
9. Sudden lack of hard drive space
Have you suddenly run out of space on your hard drive? Self-replicating viruses or worms (often called “disk bombs”) can wreak havoc on a computer system by rapidly filling hard drives with copies of itself. In many cases, the files it injects into a hard drive are invisible under default file-browsing settings.
10. Strange running processes
If your computer is acting strangely or not running as smoothly as you’d expect, type “Task Manager” into the search bar of Windows. This will list all processes consuming system resources, including rogue processes running in the background.
If an unfamiliar piece of software is consuming a disproportionate share of system resources (specifically CPU, memory and disk space), there may be a problem.
Useful tech hints:
How to deal with computer viruses and malware
When it comes to preventing computer viruses or malware infections, you should always be proactive. These best practices will help keep your computer infection-free:
Avoid unfamiliar URLs.
Compromised websites are often loaded with malware, and some top-level domains (the final part of any website’s address, or URL) are synonymous with malware.
Other widely abused TLDs include .mw, .surf, .cn and .top. If you’re “invited” to visit a website at any of these domains, especially through an unsolicited message, approach them with great caution; they are likely malware and spyware repositories.
Maintain your installed programs.
One of the primary ways viruses gain access to a system is through security lapses in existing software. A first step to prevent your computer from getting infected is to ensure your applications, antivirus software and operating system are up to date.
This is doubly important for your operating system since Apple, Microsoft and other providers regularly release security patches to deal with potential cybersecurity weaknesses. You can also reduce potential vulnerabilities for cybercriminals to exploit by uninstalling applications you don’t use.
Install only one antivirus solution.
It may seem wise to have multiple layers of antivirus protection to secure your devices from hackers, but the law of diminishing returns applies. If you have more than one antivirus software program installed on your machine, you run the risk of having them cancel each other out because each thinks the other is a virus. This can result in limited antivirus protection at best or file corruption at worst.
Note that the integrated Windows Defender utility preloaded onto PCs is designed to run alongside third-party software.
Automate virus scans.
You don’t always have to be next to your computer when it conducts a virus scan. Most modern antivirus software has automation features that let you set a specific time for the computer to run a scan. By setting the process for a time when you don’t need to use the computer – like when you’re sleeping – you can ensure your system is safe without hindering your productivity.
FAQs
1) I have virus protection, why still get virus?
A: Think of virus protection as flu vaccine protects human body. The protection rate could be close but never reach 100%. Pro Computer regularly checks malware research lab’s performance report on different virus protection software, and refer the most suitable one to match clients unique application (weight between protection rate, performance and compatibility).

2) Can you still have a virus on your computer even though your anti-virus says no?
A: Absolutely.
The terms “virus” and “malware” are often used interchangeably. However, they are technically different, so the question of malware vs. viruses is an important one.
Malware is a catch-all term for any type of malicious software, regardless of how it works, its intent, or how it’s distributed. A virus is a specific type of malware that self-replicates by inserting its code into other programs. Computer viruses have been prominent since almost the beginning of the commercial internet: The first one was created in 1982 for the Apple II, and other versions quickly followed.
Viruses spread by attaching themselves to legitimate files and programs, and are distributed through infected websites, flash drives, and emails. A victim activates a virus by opening the infected application or file. Once activated, a virus may delete or encrypt files, modify applications, or disable system functions
There are many different types of viruses. These are the three common examples:
- The file infector can burrow into executable files and spread through a network. A file infector can overwrite a computer’s operating system or even reformat its drive.
- The macro virus takes advantage of programs that support macros. Macro viruses usually arrive as Word or Excel documents attached to a spam email, or as a zipped attachment. Fake file names tempt the recipients to open the files, activating the viruses. An old but still prominent type of malware, macro viruses, remain popular with hackers.
- Polymorphic viruses modify their own code. The virus replicates and encrypts itself, changing its code just enough to evade detection by antivirus programs.
Malware encompasses all types of malicious software, including viruses, and may have a variety of goals. A few of the common objectives of malware are:
- Trick a victim into providing personal data for identity theft
- Steal consumer credit card data or other financial data
- Assume control of multiple computers to launch denial-of-service attacks against other networks
- Infect computers and use them to mine bitcoin or other cryptocurrencies
The five types of malware
Besides viruses, multiple other types of malware can infect not only desktops, laptops, and servers, but also smartphones. Malware categories include the following:
- Worms. A worm is a standalone program that can self-replicate and spread over a network. Unlike a virus, a worm spreads by exploiting a vulnerability in the infected system or through email as an attachment masquerading as a legitimate file. A graduate student created the first worm (the Morris worm) in 1988 as an intellectual exercise. Unfortunately, it replicated itself quickly and soon spread across the internet.
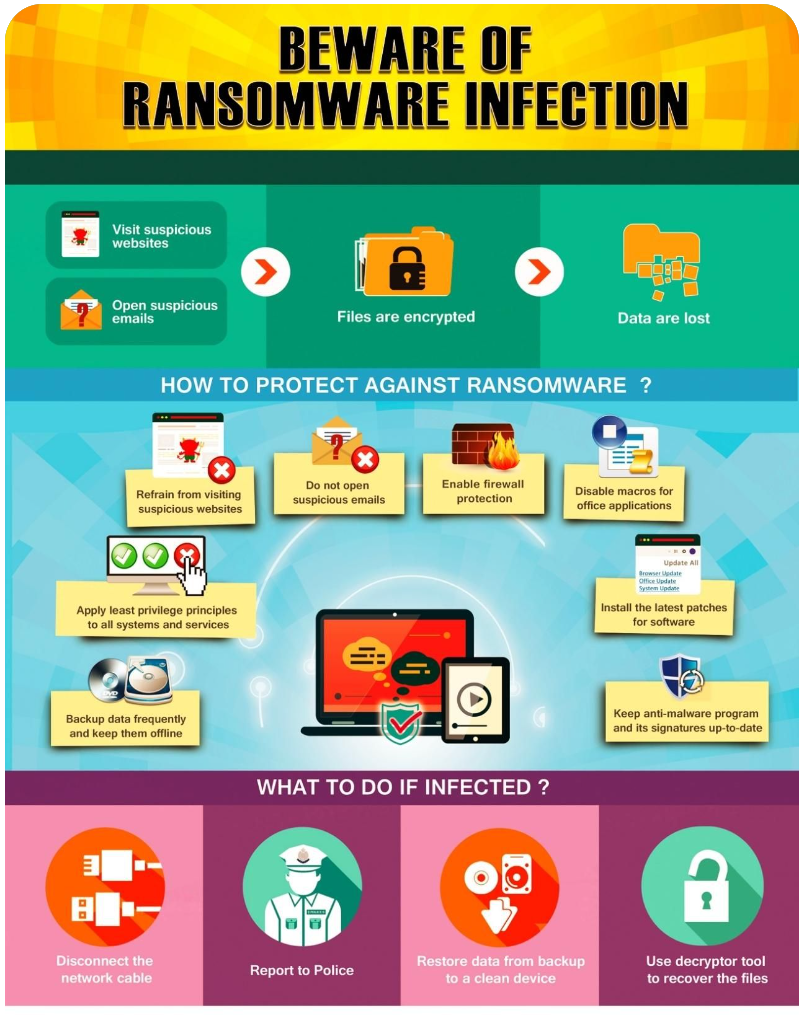
- Ransomware. As the name implies, ransomware demands that users pay a ransom—usually in bitcoin or other cryptocurrency—to regain access to their computer. The most recent category of malware is ransomware, which garnered headlines in 2016 and 2017 when ransomware infections encrypted the computer systems of major organizations and thousands of individual users around the globe.
- Scareware. Many desktop users have encountered scareware, which attempts to frighten the victim into buying unnecessary software or providing their financial data. Scareware pops up on a user’s desktop with flashing images or loud alarms, announcing that the computer has been infected. It usually urges the victim to quickly enter their credit card data and download a fake antivirus program.
- Adware and spyware. Adware pushes unwanted advertisements at users and spyware secretly collects information about the user. Spyware may record the websites the user visits, information about the user’s computer system and vulnerabilities for a future attack, or the user’s keystrokes. Spyware that records keystrokes is called a keylogger. Keyloggers steal credit card numbers, passwords, account numbers, and other sensitive data simply by logging what the user types.
- Fileless malware. Unlike traditional malware, fileless malware does not download code onto a computer, so there is no malware signature for a virus scanner to detect. Instead, fileless malware operates in the computer’s memory and may evade detection by hiding in a trusted utility, productivity tool, or security application. An example is Operation RogueRobin, which was uncovered in July 2018. RogueRobin is spread through Microsoft Excel Web Query files that are attached to an email. It causes the computer to run PowerShell command scripts, providing an attacker access to the system. As PowerShell is a trusted part of the Microsoft platform, this attack typically does not trigger a security alert. Some fileless malware is also clickless, so a victim does not need to click on the file to activate it.
There are three ways that antimalware programs have historically detected malware.
Signature analysis: Early malware (viruses, Trojan horses, etc.) were almost always static, like conventional computer programs. Any given piece of malware consisted of a certain unchanging set of bytes of computer code. Even if some parts of the malware could change, there would be some predictable pattern to it — say, the malware was composed of five parts that might be randomly reordered, but each part was always the same. So the developers of antimalware software could analyze a piece of malware and say “Okay, files with this type of malware always seem to have this sequence of thirty bytes of code in this order, and we haven’t found any other program that has those bytes in that order. So we’ll have our software block access to any file that contains those bytes in that order.” The antimalware product’s engine would have a large database of these ‘signatures’ — blocks of data that show the presence of malware — and would check files against the signature database before allowing them to run.
• Modern malware is very often “polymorphic”. That means that each copy of the malware is capable of making all sorts of random changes to itself that don’t affect its operation, but that make it look very different than other copies of the malware. There often isn’t some string of unchanging bytes that can be used as a signature — at least not without choosing a signature that’s so short that it creates an unacceptable risk of ‘false positives’ (files flagged as malware because they happen to contain a series of bytes that matches a signature, even though the file is perfectly benign).
Behavior analysis: Malware is present on your system because its developer wants it to do something, and the things that malware might be designed to do are often quite predictable, and often things that no legitimate program would be likely to do. Malware might try to write to other program files on the disk. It might try to access the Windows directory, or modify system settings, in unusual or dangerous ways. It might try to send a lot of requests to other computers on the Internet. And so on. Antimalware software can monitor programs to check to see whether they’re acting in these suspicious ways.
• Behavior analysis creates a ‘walls and ladders problem’. A developer of antimalware software has to try to check for every sort of behavior that might be suspicious — all without hurting the system’s normal functionality or annoying the user by flagging false positives. The antimalware software has to put up a wall around the whole system. Meanwhile, the malware developer just has to find one place to put up a ladder — one angle of attack that the antimalware software isn’t sufficiently checking for. When the antimalware developer builds the wall higher and thicker at that point, the malware developer looks for some other place to put up a slightly taller ladder. It’s an endless problem.
Reputational analysis: This is a newer approach, intended to deal with the problems of the previous two. The idea here is that the antimalware can generate a signature for each program that runs on the system, based on the exact contents of the program. Then the antimalware software can check a ‘reputational database’. If the database says ‘We’ve seen that program on millions of systems and it doesn’t seem to have any problems’, then the antimalware software can give the program relatively free rein. If the database says ‘We’ve only seen this program on a very small number of systems,’ then the antimalware software can apply more invasive behavior checks. And if the database says ‘We’ve seen this program on a lot of systems that seem to have malware activity,’ then the antimalware software can apply the strictest behavior checks, or jump straight to “warn the user” or even “block and quarantine the program.”
• Reputational analysis certainly helps. But of course, legitimate new programs (and legitimate new revisions of existing programs) are released all the time. So the antimalware generally can’t be too restrictive with unfamiliar programs — otherwise, the user gets annoyed and the antimalware program gets turned off or ignored — which means that there’s still room for new antimalware to maneuver and find weaknesses in the behavior analysis system.
As we can see, all of these methods have drawbacks and limitations. So inevitably, some percentage of malware is going to find its way past all of them. The best an antimalware package can do is to try to make that percentage as small as it can be without disrupting the system or annoying the user.
I came to the Pro Computer desperate & they were very helpful… not only they fixed the problem that M****t technicians could not solve…but very reasonable in price… I appreciate your superb service… Thanks …
Request a Free Quote
"*" indicates required fields
